Part 4 - Configuring Other Prerequisites¶
Installing Tanzu Mission Control Self-Managed Series¶
- Part 1 - Introduction and Environment Details
- Part 2 - Setting Up Harbor as an Image Registry
- Part 3 - Configuring Okta as Identity Provider
- Part 4 - Configuring Other Prerequisites
- Part 5 - Tanzu Kubernetes Grid Cluster Setup
- Part 6 - Installing Tanzu Mission Control Self-Managed
Configure a DNS Zone¶
TMC Self-Managed requires a DNS zone to store the DNS records to ensure proper traffic flow and access to different TMC endpoints. For example, during the authentication process redirection happens to auth and landing endpoints. If these are not configured correctly the authentication workflow will fail.
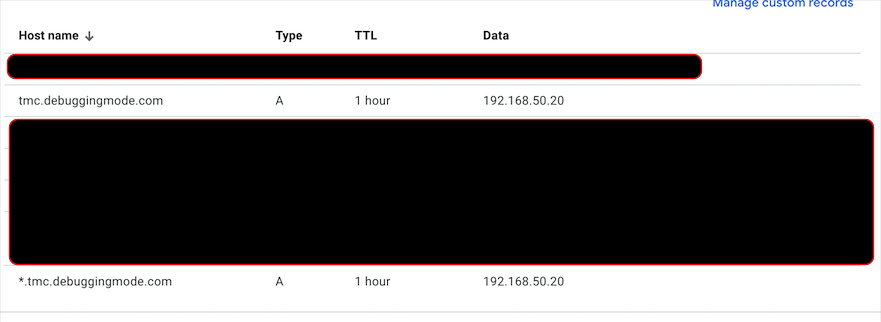
One important thing to note and that may strike you as confusing is this same DNS zone is what you will use to access TMC Self-Managed console as well. Let's dive into this with an example, in this setup my DNS zone is tmc.debuggingmode.com so the corresponding DNS entry for auth endpoint will be auth.tmc.debuggingmode.com. You will access the TMC Self-Managed using https://tmc.debuggingmode.com.
Let's assume TMC_DNS_ZONE=tmc.debuggingmode.com. You can configure DNS entries in the two ways mentioned below. You can pre-create these entries before installation with an IP. TMC Self-Managed configuration properties provide a way to assign an IP to the load balancer service created during installation.
Using a wildcard entry¶
If your DNS server supports configuring wildcard entries you can set *.TMC_DNS_ZONE to the load balancer IP front-facing TMC Self-Managed
Example Configuration from Google Domains¶
Adding individual entries for each endpoint¶
There are 12 endpoints in total that need to be set to the LoadBalancer IP. All the 12 endpoints need to resolve to the same IP